
Blog > Automation > VLANs: Why Do I Need Them?
VLANs: Why Do I Need Them?
2/7/19 | Ryan Shenk, Rexel Technical Consultant

Blog > Automation > VLANs: Why Do I Need Them?
2/7/19 | Ryan Shenk, Rexel Technical Consultant
It stands for Virtual Local Area Network. Most people have heard of a LAN or Local Area Network; a network you may have in your home to connect your laptops, cell phones, etc. Every device is part of the same LAN, also referred to as a network or subnet. The network traffic typically is all handled by a single device that performs several functions: wireless access point, Internet router, NAT (Network Address Translation), and Ethernet switch.
The obvious question becomes what does this “virtual” adjective mean. In a nutshell, VLANs allow a group of Ethernet devices (subnet) to be physically separated by many Ethernet switches but communicate as if they were all connected to the same physical Ethernet switch. In the example below, the three VLANs have devices located on separate floors. For the Engineering computers to be on the same network across multiple building floors, VLANs are used to isolate this traffic from marketing and accounting computers. Devices in different VLANs cannot communicate when only using layer 2 switches.
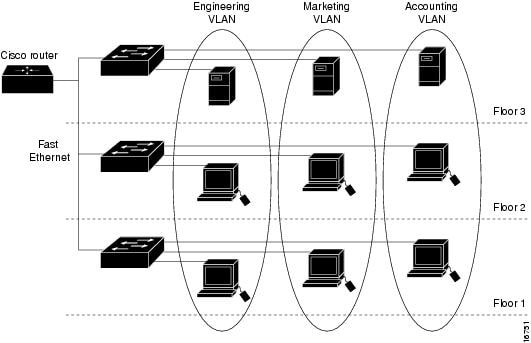
© Cisco®
Layer 2 devices only inspect the destination MAC (media access control) addresses of Ethernet frames. A MAC address is tied to a physical piece of hardware. In other words, a layer 2 switch allows devices in the same VLAN or subnet to communicate. Any VLAN-to-VLAN communication will not be allowed with just a layer 2 switch. Also, keep in mind, modern Ethernet switches often blur the lines between layer 2 and layer 3 capabilities.
You may be thinking:
Ok, so VLANs allow physical separation and a “virtual” LAN to work over several Ethernet switches. That’s all great, but I can do that by placing all devices on the same LAN. What benefits do VLANs have over making it all one large subnet?
Summed up, the question is: Why not create a large subnet instead of smaller VLANs or LANs? A single subnet is simple to understand and implement but creates problems as the network grows. By creating smaller subnets, this limits the broadcast domain traffic. Think of broadcast traffic as one device making an announcement to the rest of the devices in the network like a person speaking to a large audience, but in networking every device can speak at the same time. As more devices are added to a subnet, the “noise” or broadcast traffic increases. This may cause more latency and devices to repeat messages. When creating smaller subnets, devices that need to communicate regularly are placed on the same VLAN or subnet.
For example, a PLC (Programmable Logic Controller) and its distributed I/O (input/output), drives, etc. would be placed on the same VLAN due to the high bandwidth, multicast traffic, and fast messaging demands. Other devices that seldom require connecting to a PLC or drive would be placed in a separate VLAN.
Now, you may be thinking:
I understand that smaller VLANs or subnets are good for separating broadcast domains, but what happens when devices in different VLANs need to communicate?
A device called a router handles requests for devices to communicate when not belonging to the same VLAN. This function is called interVLAN routing. The router will have programmed an IP (Internet protocol) address on each of its connected VLAN networks. This IP address will typically be the default gateway IP address for each device on the network. The router performs the layer 3 function of inspecting the destination IP address, subnet, and VLAN. Based on the router’s information about connected networks and routes, it will forward along packets appropriately.
A best practice is to have your subnet, broadcast domain, and VLAN relationship to all be the same. That’s why these terms are interchanged frequently. They are not required to be the same, but industry standards over time have made it this way. So, don’t make them different.
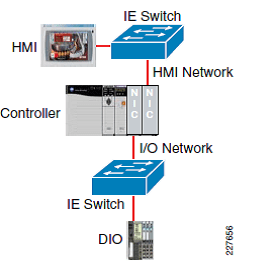
Devices with single Ethernet interfaces like CompactLogix 5370 controllers can communicate to local I/O devices and higher-level software on other networks when using VLANs and routing. Access to all devices is possible unlike when using physical segmentation like a CIP bride with two Ethernet cards using ControlLogix (see an example to the right). Modern network design with small VLANs and routing allow fewer network interface cards while maintaining segmentation. Segmentation is logically controlled because VLANs cannot communicate inherently without assistance from layer 3 devices allowing rules to be created for what devices and VLANs can communicate.
You can learn more about network architecture and get recommendations for network architectures proven to perform in the industrial controls network in Converged Plantwide Ethernet (CPwE) Design and Implementation Guide from Cisco and Rockwell Automation®.
We have Automation Specialists specializing in VLANs, LANs, CPwE, and all the acronyms that keep your operation connected and running. Our specialists offer expert guidance and design custom solutions. Contact us today!
Click Here to Download our FREE ABCs of Industrial Networks eBook
