
Blog > Automation > 70% of Ransomware Hits Manufacturing: 4 Tips to Keep Your Factory Safe
70% of Ransomware Hits Manufacturing: 4 Tips to Keep Your Factory Safe
3/19/24 | Paul Sainato, IIoT Business Development Manager
Cyberscoop highlighted a recent report by Dragos that paints a concerning picture for industrial manufacturers: over 70% of ransomware attacks in 2023 targeted the manufacturing industry. Why? The article states that digital transformation has happened at such a fast rate that many manufacturers haven’t been able to keep up with the parallel need for improved cybersecurity. This alarming trend highlights the urgent need for manufacturers to take proactive steps to secure their operations.
What is Ransomware?
Ransomware is a type of malicious software designed to block access to computer systems and data until a ransom is paid. Depending on your industry, the fallout could reach far beyond operational and financial consequences, impacting not only your bottom line, but our local communities as well.
Here are four key strategies to strengthen your cybersecurity posture:
1. Conduct Regular Cybersecurity Assessments
Don’t wait until it’s too late. Partnering with a cybersecurity expert to conduct assessments can identify gaps and weaknesses in your systems, network configuration, and security protocols. These assessments can help you prioritize risks and address the most critical issues first to mitigate a cyberattack.
2. Implement Network Segmentation
Network segmentation means dividing your network into smaller, isolated segments to limit the potential damage if one segment is compromised – effectively creating a series of “firewalls” within your network. For example, segmenting your IT network for office functions from your operational technology (OT) network that controls production processes can hinder an attack from spreading if a threat actor gains access to one of those.
Related Post: Optimizing IIoT Networks: Data Management for Manufacturers
3. Implement a Firewall Protected IDMZ
Firewalls provide a vital first line of defense, and their effectiveness can be amplified by strategically deploying them within a fortified Industrial Demilitarized Zone (IDMZ).
What is an Industrial Demilitarized Zone (IDMZ)?
An IDMZ is a secure buffer zone within a manufacturing network, separating critical production systems from everyday corporate traffic. It allows controlled communication between isolated segments, but with a focus on protecting industrial operations. This reduces attack surfaces and limits lateral movement, enhancing overall cybersecurity posture. Here’s an example of what that looks like:
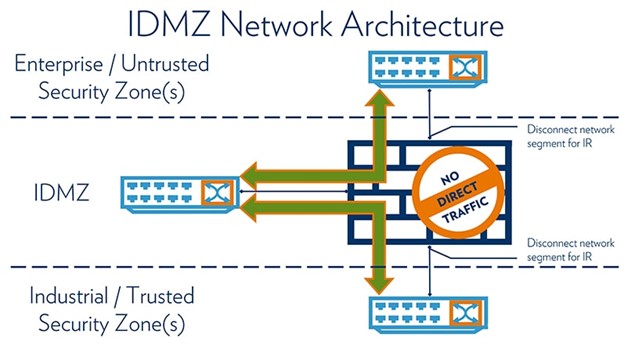
Strategically positioning firewalls at the entry and exit points of the IDMZ allows for granular control over network traffic flow. This enables you to define and enforce specific access rules, further minimizing the risk of unauthorized access. Remember, consistent updates and maintenance of firewalls within the IDMZ are crucial to ensure their effectiveness against evolving threats.
4. Foster IT/OT Collaboration
The weight of cybersecurity doesn’t solely live on the IT department’s shoulders. It requires collaborative efforts between IT and OT teams. Your IT teams understand network security best practices, and OT personnel have unique insights into the specific needs and vulnerabilities of your operational systems. When IT and OT work together, they can develop a comprehensive cybersecurity strategy tailored to the unique needs of your manufacturing environment.
Let's Recap
As the industrial manufacturing sector continues to be a primary target for threat actors, these four strategies can help you mitigate cyberattacks:
- Conduct regular cybersecurity assessments to identify and close gaps
- Implement network segmentation to isolate and neutralize threats
- Implement a firewall protected IDMZ to control communication and protect industrial operations
- Foster IT/OT collaboration to develop a comprehensive cybersecurity strategy across your manufacturing environment
Remember, cybersecurity is an ongoing process, not a one-and-done fix. As you continue your digital transformation journey, make sure you prioritize cybersecurity. It’s not a matter of if you will face a cyberattack, but when. Contact us today to get started.
Related Post: Case Study: Securing Critical Infrastructure ‘til the Cows Come Home
ABOUT US
Rexel Automation Solutions is committed to helping our customers achieve their desired business outcomes by delivering best-in-class customer experience and support.
We specialize in industrial automation services, solutions, and products that transform your application and operational needs into fully realized solutions, delivering measurable results and profitability for your company.