Water & Wastewater

Protecting Your Infrastructure
As an IT/OT professional, we understand the critical role you play in safeguarding your company's critical infrastructure. It's our mission to empower professionals like you with sustainable and innovative solutions, ensuring network visibility, advanced threat detection, and protection for your industrial operations, all while preserving your revenue streams.
Together, we can scale your IoT security, supporting you in the following areas:
- Asset Identification
- Managed Environment
- Disaster Recovery
- Securing Devices
- Industrial Networks
SUITE OF SERVICES & SOLUTIONS
Our portfolio has helped some of the world’s most successful companies mitigate risk, improve reliability, increase productivity, and augment workforces with critical competencies.


Network Monitoring & Remediation
Get in-depth visibility into device health, availability, and performance of any IP-based device in real time. Monitor network services and visualize system performance.


Routing, Switching, and Firewalls
No business or industry is safe from attack. While industrial-grade switches provide some security features, you need industrial firewalls and routers to control communication between devices and secure communication across the entire network.




Virtualization
Virtualization is essential for monitoring and functioning in an Industry 4.0 perspective. The feature of application virtualization, which allows operation beyond the operating system, is precisely the key to facilitating the path of integration with the world of embedded systems, which characterize production environments.
With network virtualization, the available bandwidth availability is divided into different channels, independent from each other, so they can be assigned to different servers or devices with advantages in complexity reduction and traffic management.


Software-Defined Access
Built on the principles of intent-based networking, SD-Access helps organizations enable policy-based automation from the edge to the cloud.
SD-Access gives network architects the tools to orchestrate key business functions like secure segmentation, IoT integration, and guest access while automating user and device policy for any application across the wireless and wired network. This allows IT to set network access in minutes for any user, device, or application, without compromising on security.



Server & Workstation
Some of the biggest challenges faced in securing ICS/OT technologies and processes include:
- Integrating legacy and aging OT with modern IT systems
- IT security technologies that cause disruption in OT environments
- Insufficient labor resources to implement existing security plans
- IT staff that does not understand OT operational requirements

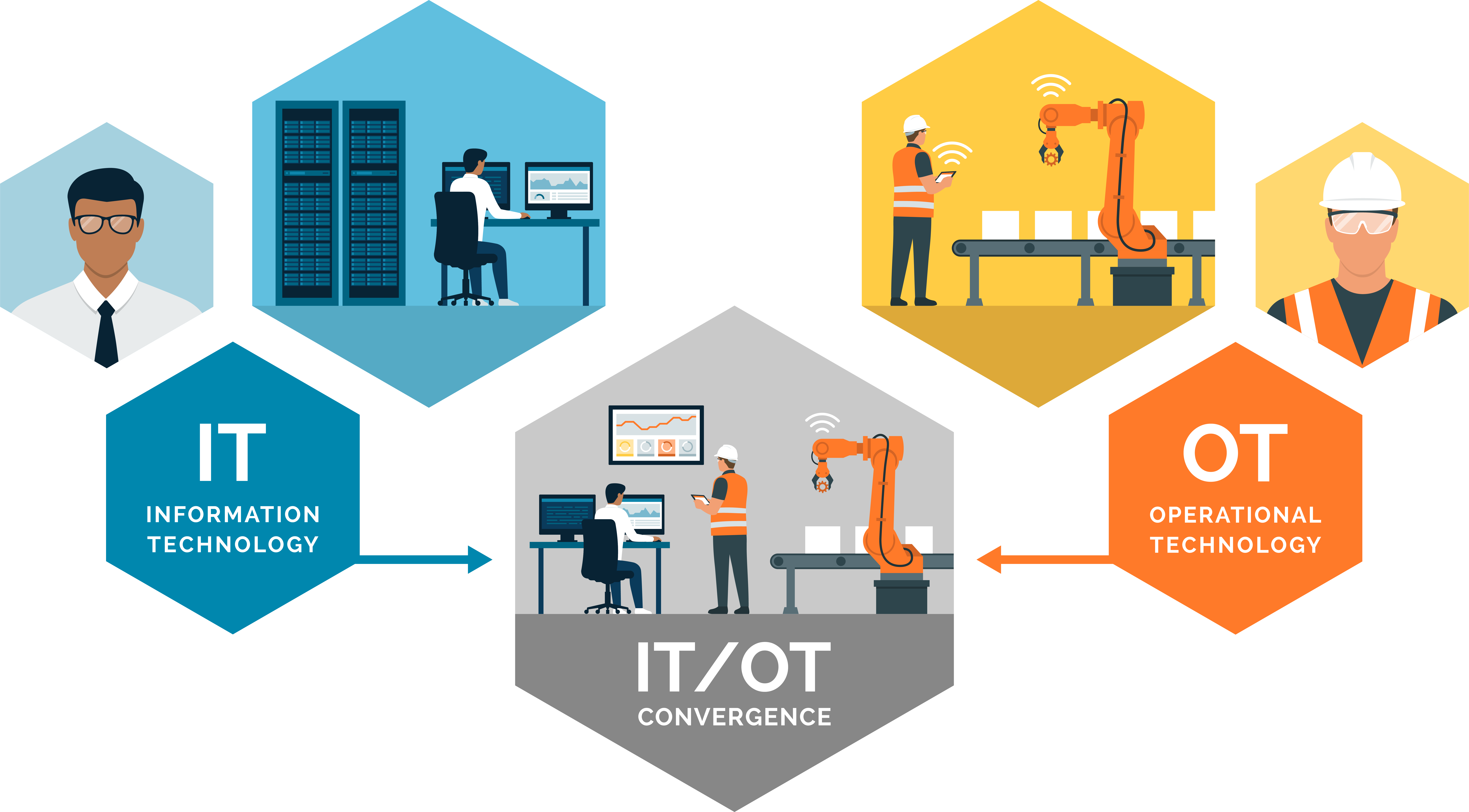
BRIDGING THE GAP
With OT and IT converging, the line between digital and physical
infrastructure becomes increasingly blurred, leaving industrial
manufacturers vulnerable to cyberattacks. To implement successful risk mitigation strategies, the IT and OT teams must work together with clear objectives, and that's where we developed our unique expertise, helping manufacturers overcome challenges and achieve desired outcomes:
- Increase visibility and control of plant floor assets
- Reduce vulnerabilities to the industrial network
- Improve mitigation and remediation tactics
- Implement comprehensive and easy-to-use solutions
- Minimize the skills gap of both IT & OT departments
- Improve reliability of industrial network and connected assets
- Maintain uptime and production
IS YOUR BUSINESS PROTECTED?
In today’s world, it’s not a question of if your business will be subjected to a cybercrime, it’s when. Do you have the necessary precautions in place to stop a cyberattack from happening? Are you ready to respond immediately to help mitigate the effects of a cyber incident?
Our Cybersecurity Preparedness Assessment will help you decide what areas you need to prioritize and how
to implement industrial cybersecurity best practices in your organization.
Upon completion of the assessment, we will provide you with your Cybersecurity Preparedness Score based
on the NIST Cybersecurity Framework. You will also receive a fully customized report that will allow you to
dive into your results, get recommendations on how to improve your score, and compare yourself to
industry averages.


Trusted Partners
We use our extensive knowledge base and partnerships to address the sophisticated challenges of the industrial automation market. Our portfolio of services and solutions has helped countless organizations improve their risk mitigation strategies.









Our list of partners and suppliers doesn't stop here. Learn more about the full-scope offering you can trust us to deliver.

SERVING YOU IN THE MARKET
Food & Beverage
Manufacturing
Mining
Utilities
Life Sciences
Entertainment
System Integrators
Don't wait, scale your IIoT security with Rexel today.
ABOUT US
Rexel Automation Solutions is committed to helping our customers achieve their desired business outcomes by delivering best in class customer experience and support.
We specialize in industrial automation services and solutions delivering measurable results for your company.
NEWSLETTER

5429 Lyndon B Johnson Fwy #600, Dallas, TX 75240
© Copyright 2024 Rexel USA, Inc. All Rights Reserved
